System standard
Ljus
Mörk
System standard
System standard
Ljus
Mörk
Författare
Anton Wasmuth
SOC @ Asurgent
Read time
2 min
15 November 2023
Adversary-in-the-middle (AiTM) phishing

What is an Adversary in the Middle attack?
The techniques used in phishing attacks continue to increase in complexity. Although Multi-Factor Authentication (MFA) adds an additional security layer to combat credential theft attackers are discovering innovative techniques to bypass these extra security measures, including both MFA and 2FA. AitM attacks commonly start with a phishing email that looks as though it is from a legitimate source. The phishing email typically contains hidden HTML elements (like malicious links embedded into buttons) that connect to a fraudulent web page.
How it works?
An attacker will use a proxy server that is deployed between the victim and the website they are attempting to access. This allows the attacker to intercept the victim's login credentials and session for the targeted website. The user enters their credentials and completes MFA and are then directed to any other website. After this the attacker capturing credentials and session cookies. Obtaining tokens could allow an attacker to bypass controls such as conditional access and MFA.

What about QR-codes in AiTM attacks (Qishing)
Even if Adversary-in-the-Middle (AiTM) phishing, have been used for several years. Asurgent Security Operations Center (SOC) have observed phishing incidents where attackers have used QR codes that leads the victim to a AiTM or redirect website to: (bing/baidu). QR-codes are used because it forces the victim to enter the AiTM site from their mobile device where they are less likely to have endpoint protection that blocks the connection or warns the user of malicious content.
The widespread accessibility of QR code generators on the internet, has made them a potentially attractive tool by cybercriminals.

Technial overview
Evilginx is a man-in-the-middle attack framework that is open source and is also one of the most popular AiTM tools.
For testing purposes and to demonstrate how the attack is performed we purchased a domain and deployed an Ubuntu server in Azure that we used to host our Evilginx phishing site.
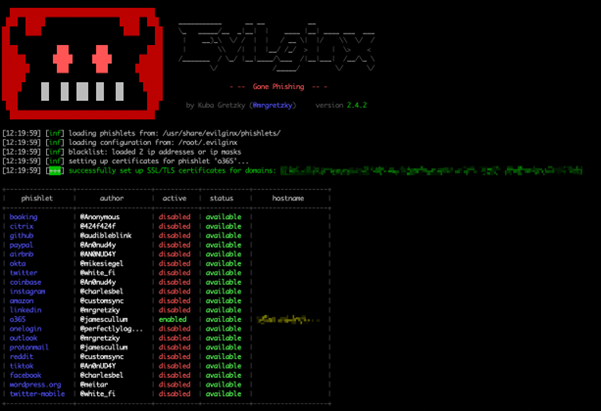
1. Victim receives QR code with malicious URL pointing to AiTM phishing site.

2. Branded sign-in page as the request is proxied and sent to the real Microsoft sign in to be intercepted.
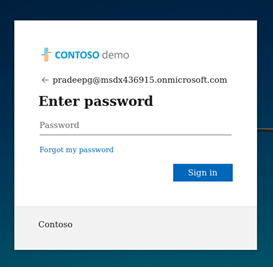
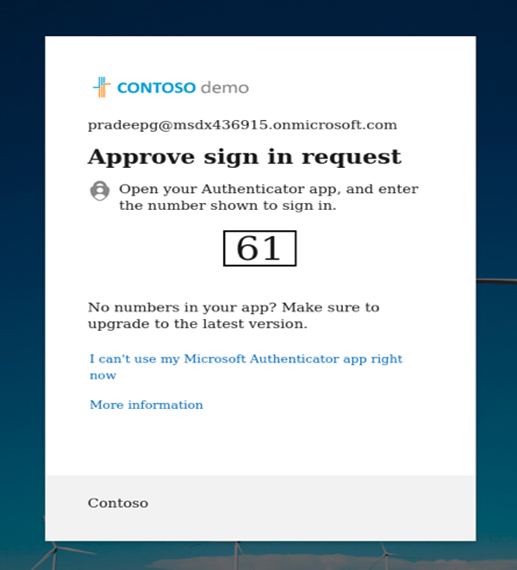
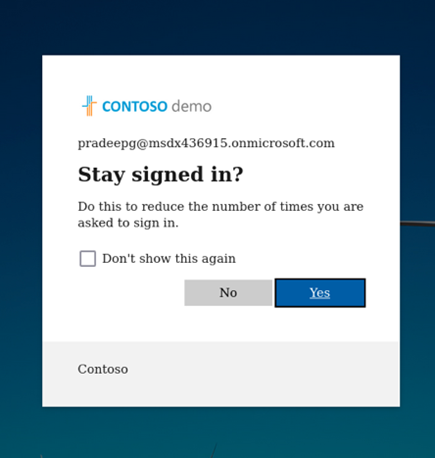
3. After user has completed sign in flow the user is redirected to URL configured in evilginx. In this example the redirect URL was portal.office.com
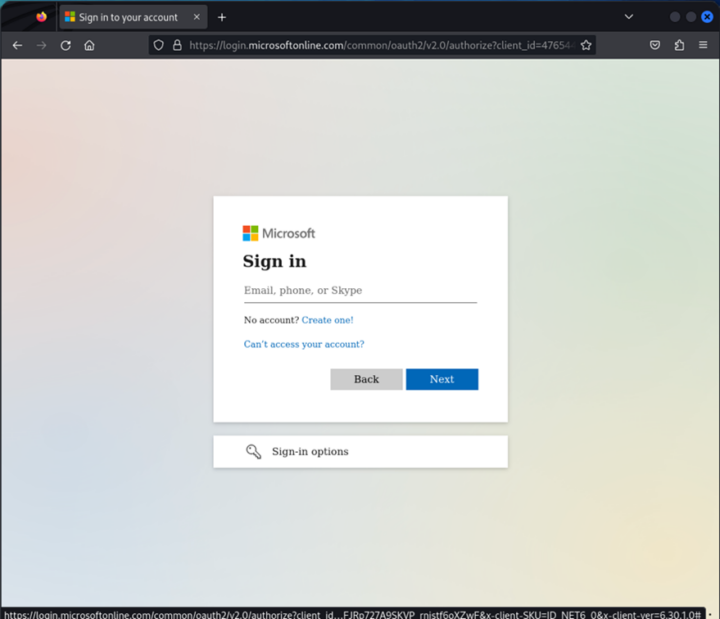
4. The token and the users’ credentials are captured.
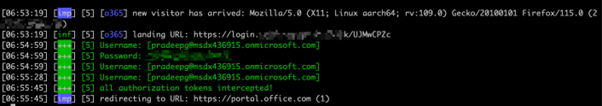
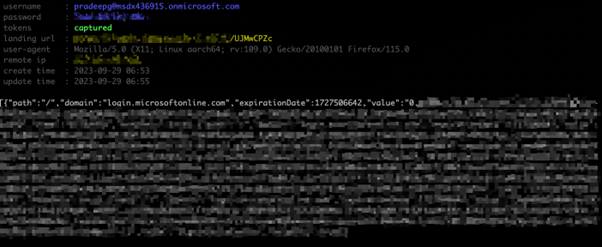
5. After the credentials are captured the attacker can easily use the session cookie to sign in as the compromised user and bypass MFA since the claim is included in the token.
Prevention
Educate users regarding the dangers of QR code phishing emails.
Deploy security for mobile devices utilized for accessing enterprise resources.
Utilize security defaults as a fundamental set of policies to enhance identity security.
For more comprehensive protection, enable conditional access policies, particularly risk-based policies from Microsoft Entra ID protection.
These conditional access policies assess sign-in requests by considering additional identity-related factors such as user or group memberships, IP address location data, and device status, among others, these policies can block sign-in if the risk is determined to be high.
If you are using Microsoft Sentinel it is also possible to monitor suspicious activity after a risky sign in, for example any change to the user's authentication methods. We have observed that this is a common tactic to maintain persistence in an environment.
M365D customers can enable web content filtering to block new registered domains and therefore minimise the risk of connect to malicious domains. Consider integrating Azure Active Directory Phishing-resistant MFA strength - includes methods that require an interaction between the authentication method and the sign-in surface as the picture below describes.

Prenumerera på vårt nyhetsbrev för att ha koll på senaste nytt inom molnsfären.